NFC Security Bag including the NFC smartphone app for optimal tracking and storage with tamper protection – first look available at GPEC from September 9th – 11th 2014, Stand C67 in H1.
New release available now from ENAiKOON, NFC Security Bag and the coordinating NFC smartphone app with integration into inViu web, ENAiKOON’s highly secure telematics platform.
Typical use cases
Security bags with an integrated NFC tag are particularly suitable for the safe transport and professional storage and safekeeping of important objects, including tamper protection. The following are examples of typical use case for these security bags:
• Confidential and important document transfer
• Transport of high value goods
• Equipment security policy for weapons, illegal narcotics, and other restricted access items
• Transport of urine and blood samples for doping tests
• Chain of custody drug testing
• Forensic evidence collection and storage
• Personal property bags for patients in hospitals or deceased individuals
• Inmate personal property inventory
• Chain of custody for expensive or dangerous pharmaceutical, biological or chemical products
• Secure data disposal to verify the destruction or hard drives or other storage devices with important data from banks, power plants, and other facilities which are not connected to the internet
• and many more
Lost or altered items are now a thing of the past.
Typical requirements
• Error-free and 100% traceable documented tracking for transport of critical objects
• Complete documentation of the contents, storage area as well as the responsible person in each case for the NFC security bag
• Management of additional information as needed for each security bag including for example comments, photos, audio notes, videos, electronic signature capture, etc.
• Evidence of tampering, changing or tampering with the contents of the security bag are evident and able to be identified
Features of the NFC security bag
NFC tag for tamper proof identification
The high tech NFC security bags from ginstr are equipped with an NFC tag and are more secure than the current bags on the market using bar-codes or written information.
With the NFC tag the NFC security bag and the associated information is saved in a databank using a smartphone app. By simply reading the NFC tag an approved smartphone is able to access all relevant data concerning the associated NFC security bag.
In addition to the collecting and reading the NFC security bag information photos, videos, electronic signature capture, audio notes, comments, etc. can be centrally stored and recalled later.
Consecutive serial numbers
In addition to NFC tags the NFC security bags have consecutive serial numbers that are tamper proof and stored on the NFC tag. The serial numbers are unique per customer and the NFC tags are globally unique. Thus, neither can a security bag be missed nor another organisations security bags used.
Tamper evident closure
The NFC security bag cannot be opened without destroying it. Attacks by heat, cold, or attempts to close a bag which has been opened are recognisable due to obvious signs of tampering.
Removable ownership receipt
With this record the owner of the contents can prove ownership or the sender of the bag that it is shipped.
Customisable printing
The NFC security bag can be printed with your logo and any additional fields as needed for your organisation.
A variety of sizes and optional extras
The NFC security bags can be produced in different sizes.
Standard sizes are 152×228 mm (6×9 inches), 228×304 mm (9×12 inches), 304 x457 mm (12×18 inches), 381×508 mm (15×20 inches)
The security bags can be produced in different versions, for example with an antistatic coating for hard drives and other storage devices.
Price
Depending on the quantity ordered the cost of NFC Security Bags ranges from €2.90 – €4.90 per unit. The monthly subscription fee for the use of the smartphone app and back end administration software, including data storage on ENAiKOON’s highly secure servers, costs €9.90 per month per user with a minimum contract length of 24 months. All prices are excluding VAT.
More information about prices
More informationen
Read more on the ginstr website about use cases and functions.
Category Archives: Theft Prevention
Fuel theft: detection and prevention
With no sign of fuel prices going down, fuel theft continues to grow in all
parts of the globe. In recent news, Brentwood and Chelmsford in the UK,
experienced thousands of litres of diesel siphoned out of 8 lorries
during the drivers’ break. In the Philippines, employees of the Metropolitan Manila Development Authority have
been arrested for selling diesel fuel siphoned from their work vehicle.
None of this would have happened if the vehicles were properly equipped with an
anti-fuel-theft system. Unmonitored vehicles are left vulnerable to fuel theft,
and the surveillance of fuel tank level becomes critical to catching thieves in
their act.
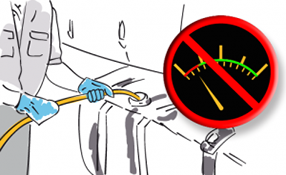 Any reputable anti-fuel-theft system should monitor fuel consumption, for
both fuel theft prevention and fuel efficiency. Continuous monitoring of fuel
consumption and appropriate driver training can save 10% on fuel costs. With
diesel thieves being capable of stealing up to €1,000 worth of fuel, a
comprehensive system that can save fuel costs and stop diesel theft is well
worth the investment for any company that owns a fleet of vehicles.
Any reputable anti-fuel-theft system should monitor fuel consumption, for
both fuel theft prevention and fuel efficiency. Continuous monitoring of fuel
consumption and appropriate driver training can save 10% on fuel costs. With
diesel thieves being capable of stealing up to €1,000 worth of fuel, a
comprehensive system that can save fuel costs and stop diesel theft is well
worth the investment for any company that owns a fleet of vehicles.
 Investing in the right system is exactly what one transport company in
Southern Germany did after a series of fuel theft incidents. The company, who
wishes to remain anonymous for security reasons, chose ENAiKOON’s
anti-fuel-theft system to catch their diesel thief. They experienced 10 cases
in an isolated truck transport site, where they installed surveillance cameras.
Even with cameras, the thief continued his work and the company was unable to
identify the offender. Finally, the local police stepped in and monitored the
site for several weeks, but even that was unsuccessful.
Their last resort was the use of ENAiKOON’s telematics solution. The system
was installed on their trucks in the summer of 2010. The results were
immediate. Shortly after the installation, the company’s management received a
text message (SMS) alert, informing them of an acute deceleration of fuel from
one of their trucks. Knowing that the thief caught the bait, management
contacted the police right away, whom were able to catch the crook in
action.
The ability to monitor remotely and in real time using their smartphone has
allowed this company to react fast enough to stop the crime. ENAiKOON can also
help with other fleet management needs, such as vehicle maintenance, driving
behaviour, dispatcher communication, and driver coordination. Contact
ENAiKOON for further information on how to stop fuel theft and increase
fuel efficiency or check out www.stop-fuel-theft.net.
Investing in the right system is exactly what one transport company in
Southern Germany did after a series of fuel theft incidents. The company, who
wishes to remain anonymous for security reasons, chose ENAiKOON’s
anti-fuel-theft system to catch their diesel thief. They experienced 10 cases
in an isolated truck transport site, where they installed surveillance cameras.
Even with cameras, the thief continued his work and the company was unable to
identify the offender. Finally, the local police stepped in and monitored the
site for several weeks, but even that was unsuccessful.
Their last resort was the use of ENAiKOON’s telematics solution. The system
was installed on their trucks in the summer of 2010. The results were
immediate. Shortly after the installation, the company’s management received a
text message (SMS) alert, informing them of an acute deceleration of fuel from
one of their trucks. Knowing that the thief caught the bait, management
contacted the police right away, whom were able to catch the crook in
action.
The ability to monitor remotely and in real time using their smartphone has
allowed this company to react fast enough to stop the crime. ENAiKOON can also
help with other fleet management needs, such as vehicle maintenance, driving
behaviour, dispatcher communication, and driver coordination. Contact
ENAiKOON for further information on how to stop fuel theft and increase
fuel efficiency or check out www.stop-fuel-theft.net.
 Any reputable anti-fuel-theft system should monitor fuel consumption, for
both fuel theft prevention and fuel efficiency. Continuous monitoring of fuel
consumption and appropriate driver training can save 10% on fuel costs. With
diesel thieves being capable of stealing up to €1,000 worth of fuel, a
comprehensive system that can save fuel costs and stop diesel theft is well
worth the investment for any company that owns a fleet of vehicles.
Any reputable anti-fuel-theft system should monitor fuel consumption, for
both fuel theft prevention and fuel efficiency. Continuous monitoring of fuel
consumption and appropriate driver training can save 10% on fuel costs. With
diesel thieves being capable of stealing up to €1,000 worth of fuel, a
comprehensive system that can save fuel costs and stop diesel theft is well
worth the investment for any company that owns a fleet of vehicles.
 Investing in the right system is exactly what one transport company in
Southern Germany did after a series of fuel theft incidents. The company, who
wishes to remain anonymous for security reasons, chose ENAiKOON’s
anti-fuel-theft system to catch their diesel thief. They experienced 10 cases
in an isolated truck transport site, where they installed surveillance cameras.
Even with cameras, the thief continued his work and the company was unable to
identify the offender. Finally, the local police stepped in and monitored the
site for several weeks, but even that was unsuccessful.
Their last resort was the use of ENAiKOON’s telematics solution. The system
was installed on their trucks in the summer of 2010. The results were
immediate. Shortly after the installation, the company’s management received a
text message (SMS) alert, informing them of an acute deceleration of fuel from
one of their trucks. Knowing that the thief caught the bait, management
contacted the police right away, whom were able to catch the crook in
action.
The ability to monitor remotely and in real time using their smartphone has
allowed this company to react fast enough to stop the crime. ENAiKOON can also
help with other fleet management needs, such as vehicle maintenance, driving
behaviour, dispatcher communication, and driver coordination. Contact
ENAiKOON for further information on how to stop fuel theft and increase
fuel efficiency or check out www.stop-fuel-theft.net.
Investing in the right system is exactly what one transport company in
Southern Germany did after a series of fuel theft incidents. The company, who
wishes to remain anonymous for security reasons, chose ENAiKOON’s
anti-fuel-theft system to catch their diesel thief. They experienced 10 cases
in an isolated truck transport site, where they installed surveillance cameras.
Even with cameras, the thief continued his work and the company was unable to
identify the offender. Finally, the local police stepped in and monitored the
site for several weeks, but even that was unsuccessful.
Their last resort was the use of ENAiKOON’s telematics solution. The system
was installed on their trucks in the summer of 2010. The results were
immediate. Shortly after the installation, the company’s management received a
text message (SMS) alert, informing them of an acute deceleration of fuel from
one of their trucks. Knowing that the thief caught the bait, management
contacted the police right away, whom were able to catch the crook in
action.
The ability to monitor remotely and in real time using their smartphone has
allowed this company to react fast enough to stop the crime. ENAiKOON can also
help with other fleet management needs, such as vehicle maintenance, driving
behaviour, dispatcher communication, and driver coordination. Contact
ENAiKOON for further information on how to stop fuel theft and increase
fuel efficiency or check out www.stop-fuel-theft.net. Equipment, employee, and vehicle tracking in the construction industry
Every year, billions of dollars’ worth of construction equipment is stolen
around the world with only a 10-20% recovery rate. Monitoring and protecting
your assets is vital to any organisation in any industry, and construction is
no exception. With heavy equipment and machinery averaging at ,000 USD each,
we cannot afford to leave construction sites poorly secured. A comprehensive telematics system is the perfect
solution with many additional benefits. Not only will it protect your assets
from theft, but it will also improve maintenance, project planning, task
management, employee productivity, and fuel consumption.
 The GPS tracking device attached to vehicles, machinery, and equipment will
collect their location information as well as CAN-bus, driver behaviour, and
fuel level data. Analysing this data will allow you to optimise maintenance
schedules that will minimise vehicle down time, reduce fuel consumption, detect
fuel theft, and minimise costs on repairs and excess fuel – all leading to a
better bottom-line. Knowing how long tasks take to complete will help you plan
project timelines better, and this increase in efficiency will open up more
time for you to focus on the daily operations of your construction company.
ENAiKOON has a trusted telematics solution that has been tried and tested by
many construction companies. Here is what one of their customers had to say
about their construction equipment monitoring system:
Construction equipment monitoring at Rühlmann-Bau
Rühlmann-Bau is a medium-sized construction company in
Saxony-Anhalt, Germany. They have a large, modern machine park with a variety
of specialised equipment, such as horizontal and vertical drills and asphalt
packers. In total, there are about 120 units in constant use which need to be
correctly coordinated and protected from theft. The more staff they have on the
road, the more important it is for the smooth communication between the
dispatcher and foreman at various construction sites.
In March 2009, the first machinery equipped with the ENAiKOON starter
package was tested. The benefits of construction equipment monitoring were
quickly recognised by Uwe Rühlmann, CEO of Rühlmann-Bau. “For me, it is
important to have all of our units equipped with ENAiKOON devices,” says Mr.
Rühlmann. “First, because I can coordinate and control what is being deployed
better and where it is at all times, and second, because I want to treat all of
my drivers equally.” That following May, Mr. Rühlmann implemented the devices
on all company machinery and since then have not experienced any theft or
misuse.
The ENAiKOON construction equipment monitoring solution
Every construction company has to protect their assets, whether it’s
equipment, vehicles, or their people. Whatever your needs may be, ask an
ENAiKOON telematics expert for advice on equipment security using their
reliable range of devices and software. Manage your assets and people better so
that you can decrease costs and eliminate theft. Contact ENAiKOON
today for your free trial.
The GPS tracking device attached to vehicles, machinery, and equipment will
collect their location information as well as CAN-bus, driver behaviour, and
fuel level data. Analysing this data will allow you to optimise maintenance
schedules that will minimise vehicle down time, reduce fuel consumption, detect
fuel theft, and minimise costs on repairs and excess fuel – all leading to a
better bottom-line. Knowing how long tasks take to complete will help you plan
project timelines better, and this increase in efficiency will open up more
time for you to focus on the daily operations of your construction company.
ENAiKOON has a trusted telematics solution that has been tried and tested by
many construction companies. Here is what one of their customers had to say
about their construction equipment monitoring system:
Construction equipment monitoring at Rühlmann-Bau
Rühlmann-Bau is a medium-sized construction company in
Saxony-Anhalt, Germany. They have a large, modern machine park with a variety
of specialised equipment, such as horizontal and vertical drills and asphalt
packers. In total, there are about 120 units in constant use which need to be
correctly coordinated and protected from theft. The more staff they have on the
road, the more important it is for the smooth communication between the
dispatcher and foreman at various construction sites.
In March 2009, the first machinery equipped with the ENAiKOON starter
package was tested. The benefits of construction equipment monitoring were
quickly recognised by Uwe Rühlmann, CEO of Rühlmann-Bau. “For me, it is
important to have all of our units equipped with ENAiKOON devices,” says Mr.
Rühlmann. “First, because I can coordinate and control what is being deployed
better and where it is at all times, and second, because I want to treat all of
my drivers equally.” That following May, Mr. Rühlmann implemented the devices
on all company machinery and since then have not experienced any theft or
misuse.
The ENAiKOON construction equipment monitoring solution
Every construction company has to protect their assets, whether it’s
equipment, vehicles, or their people. Whatever your needs may be, ask an
ENAiKOON telematics expert for advice on equipment security using their
reliable range of devices and software. Manage your assets and people better so
that you can decrease costs and eliminate theft. Contact ENAiKOON
today for your free trial.
 The GPS tracking device attached to vehicles, machinery, and equipment will
collect their location information as well as CAN-bus, driver behaviour, and
fuel level data. Analysing this data will allow you to optimise maintenance
schedules that will minimise vehicle down time, reduce fuel consumption, detect
fuel theft, and minimise costs on repairs and excess fuel – all leading to a
better bottom-line. Knowing how long tasks take to complete will help you plan
project timelines better, and this increase in efficiency will open up more
time for you to focus on the daily operations of your construction company.
ENAiKOON has a trusted telematics solution that has been tried and tested by
many construction companies. Here is what one of their customers had to say
about their construction equipment monitoring system:
Construction equipment monitoring at Rühlmann-Bau
Rühlmann-Bau is a medium-sized construction company in
Saxony-Anhalt, Germany. They have a large, modern machine park with a variety
of specialised equipment, such as horizontal and vertical drills and asphalt
packers. In total, there are about 120 units in constant use which need to be
correctly coordinated and protected from theft. The more staff they have on the
road, the more important it is for the smooth communication between the
dispatcher and foreman at various construction sites.
In March 2009, the first machinery equipped with the ENAiKOON starter
package was tested. The benefits of construction equipment monitoring were
quickly recognised by Uwe Rühlmann, CEO of Rühlmann-Bau. “For me, it is
important to have all of our units equipped with ENAiKOON devices,” says Mr.
Rühlmann. “First, because I can coordinate and control what is being deployed
better and where it is at all times, and second, because I want to treat all of
my drivers equally.” That following May, Mr. Rühlmann implemented the devices
on all company machinery and since then have not experienced any theft or
misuse.
The ENAiKOON construction equipment monitoring solution
Every construction company has to protect their assets, whether it’s
equipment, vehicles, or their people. Whatever your needs may be, ask an
ENAiKOON telematics expert for advice on equipment security using their
reliable range of devices and software. Manage your assets and people better so
that you can decrease costs and eliminate theft. Contact ENAiKOON
today for your free trial.
The GPS tracking device attached to vehicles, machinery, and equipment will
collect their location information as well as CAN-bus, driver behaviour, and
fuel level data. Analysing this data will allow you to optimise maintenance
schedules that will minimise vehicle down time, reduce fuel consumption, detect
fuel theft, and minimise costs on repairs and excess fuel – all leading to a
better bottom-line. Knowing how long tasks take to complete will help you plan
project timelines better, and this increase in efficiency will open up more
time for you to focus on the daily operations of your construction company.
ENAiKOON has a trusted telematics solution that has been tried and tested by
many construction companies. Here is what one of their customers had to say
about their construction equipment monitoring system:
Construction equipment monitoring at Rühlmann-Bau
Rühlmann-Bau is a medium-sized construction company in
Saxony-Anhalt, Germany. They have a large, modern machine park with a variety
of specialised equipment, such as horizontal and vertical drills and asphalt
packers. In total, there are about 120 units in constant use which need to be
correctly coordinated and protected from theft. The more staff they have on the
road, the more important it is for the smooth communication between the
dispatcher and foreman at various construction sites.
In March 2009, the first machinery equipped with the ENAiKOON starter
package was tested. The benefits of construction equipment monitoring were
quickly recognised by Uwe Rühlmann, CEO of Rühlmann-Bau. “For me, it is
important to have all of our units equipped with ENAiKOON devices,” says Mr.
Rühlmann. “First, because I can coordinate and control what is being deployed
better and where it is at all times, and second, because I want to treat all of
my drivers equally.” That following May, Mr. Rühlmann implemented the devices
on all company machinery and since then have not experienced any theft or
misuse.
The ENAiKOON construction equipment monitoring solution
Every construction company has to protect their assets, whether it’s
equipment, vehicles, or their people. Whatever your needs may be, ask an
ENAiKOON telematics expert for advice on equipment security using their
reliable range of devices and software. Manage your assets and people better so
that you can decrease costs and eliminate theft. Contact ENAiKOON
today for your free trial. Improved operations with telematics for construction equipment rental companies
Equipment rental is a relatively new yet rapidly growing industry with some
international companies turning over €1 billion annually. The reasons behind
its popularity are capital release, range of equipment availability,
maintenance, and compliance with standards and regulations. This explains the
uptick in telematics sales within this industry, as GPS tracking of equipment
can help with the latter two reasons.
 A comprehensive telematics system for construction equipment can retrieve
all the necessary data to run a flawless maintenance program. The equipment
data collected and its analysis make complying with regulations a breeze.
Furthermore, having an accurate log of equipment use and location allows rental
companies to run a smooth operation. Let’s take a look at how Eberle-Hald
improved their business with ENAiKOON’s equipment monitoring system.
Construction equipment rental management at Eberle-Hald
A comprehensive telematics system for construction equipment can retrieve
all the necessary data to run a flawless maintenance program. The equipment
data collected and its analysis make complying with regulations a breeze.
Furthermore, having an accurate log of equipment use and location allows rental
companies to run a smooth operation. Let’s take a look at how Eberle-Hald
improved their business with ENAiKOON’s equipment monitoring system.
Construction equipment rental management at Eberle-Hald
 Eberle-Hald is one of the biggest construction equipment rental companies in
Stuttgart, southern Germany. They have been using ENAiKOON’s telematics
solution since 2007. Since then, more than 300 GPS devices are being used at
nine different branches. “Access to equipment data, such as operating hours,
battery condition, and loading times, at any time is of the utmost importance
to us,” says Michael Busch, the company’s rental manager. “If technical
problems occur, our emergency service staff will need to quickly identify the
problem in order to make the equipment operational again.”
The ENAiKOON telematics system enabled them to produce precise rental
contracts and customer invoices by knowing exactly where the equipment is
located along with its time stamp. With inViu pro, the rental company receives real-time alerts and
information on their rented equipment, and having an accurate account of
equipment availability helped streamline their operations. Eberle-Hald even
took ENAiKOON’s inViu pro web portal one step further and integrated it for
their customers to use. They gave their customers the option to see which
equipment at which site is currently being used, allowing their renters to have
the complete billing information to give to their own clients.
The ENAiKOON construction equipment monitoring solution
The flexible telematics solution that ENAiKOON offers can be tailored to
each customer as exemplified in the above case. Start saving time, increase
productivity, and improve rental equipment management with the construction equipment
monitoring system. Contact ENAiKOON
today for your free trial.
Eberle-Hald is one of the biggest construction equipment rental companies in
Stuttgart, southern Germany. They have been using ENAiKOON’s telematics
solution since 2007. Since then, more than 300 GPS devices are being used at
nine different branches. “Access to equipment data, such as operating hours,
battery condition, and loading times, at any time is of the utmost importance
to us,” says Michael Busch, the company’s rental manager. “If technical
problems occur, our emergency service staff will need to quickly identify the
problem in order to make the equipment operational again.”
The ENAiKOON telematics system enabled them to produce precise rental
contracts and customer invoices by knowing exactly where the equipment is
located along with its time stamp. With inViu pro, the rental company receives real-time alerts and
information on their rented equipment, and having an accurate account of
equipment availability helped streamline their operations. Eberle-Hald even
took ENAiKOON’s inViu pro web portal one step further and integrated it for
their customers to use. They gave their customers the option to see which
equipment at which site is currently being used, allowing their renters to have
the complete billing information to give to their own clients.
The ENAiKOON construction equipment monitoring solution
The flexible telematics solution that ENAiKOON offers can be tailored to
each customer as exemplified in the above case. Start saving time, increase
productivity, and improve rental equipment management with the construction equipment
monitoring system. Contact ENAiKOON
today for your free trial.
 A comprehensive telematics system for construction equipment can retrieve
all the necessary data to run a flawless maintenance program. The equipment
data collected and its analysis make complying with regulations a breeze.
Furthermore, having an accurate log of equipment use and location allows rental
companies to run a smooth operation. Let’s take a look at how Eberle-Hald
improved their business with ENAiKOON’s equipment monitoring system.
Construction equipment rental management at Eberle-Hald
A comprehensive telematics system for construction equipment can retrieve
all the necessary data to run a flawless maintenance program. The equipment
data collected and its analysis make complying with regulations a breeze.
Furthermore, having an accurate log of equipment use and location allows rental
companies to run a smooth operation. Let’s take a look at how Eberle-Hald
improved their business with ENAiKOON’s equipment monitoring system.
Construction equipment rental management at Eberle-Hald
 Eberle-Hald is one of the biggest construction equipment rental companies in
Stuttgart, southern Germany. They have been using ENAiKOON’s telematics
solution since 2007. Since then, more than 300 GPS devices are being used at
nine different branches. “Access to equipment data, such as operating hours,
battery condition, and loading times, at any time is of the utmost importance
to us,” says Michael Busch, the company’s rental manager. “If technical
problems occur, our emergency service staff will need to quickly identify the
problem in order to make the equipment operational again.”
The ENAiKOON telematics system enabled them to produce precise rental
contracts and customer invoices by knowing exactly where the equipment is
located along with its time stamp. With inViu pro, the rental company receives real-time alerts and
information on their rented equipment, and having an accurate account of
equipment availability helped streamline their operations. Eberle-Hald even
took ENAiKOON’s inViu pro web portal one step further and integrated it for
their customers to use. They gave their customers the option to see which
equipment at which site is currently being used, allowing their renters to have
the complete billing information to give to their own clients.
The ENAiKOON construction equipment monitoring solution
The flexible telematics solution that ENAiKOON offers can be tailored to
each customer as exemplified in the above case. Start saving time, increase
productivity, and improve rental equipment management with the construction equipment
monitoring system. Contact ENAiKOON
today for your free trial.
Eberle-Hald is one of the biggest construction equipment rental companies in
Stuttgart, southern Germany. They have been using ENAiKOON’s telematics
solution since 2007. Since then, more than 300 GPS devices are being used at
nine different branches. “Access to equipment data, such as operating hours,
battery condition, and loading times, at any time is of the utmost importance
to us,” says Michael Busch, the company’s rental manager. “If technical
problems occur, our emergency service staff will need to quickly identify the
problem in order to make the equipment operational again.”
The ENAiKOON telematics system enabled them to produce precise rental
contracts and customer invoices by knowing exactly where the equipment is
located along with its time stamp. With inViu pro, the rental company receives real-time alerts and
information on their rented equipment, and having an accurate account of
equipment availability helped streamline their operations. Eberle-Hald even
took ENAiKOON’s inViu pro web portal one step further and integrated it for
their customers to use. They gave their customers the option to see which
equipment at which site is currently being used, allowing their renters to have
the complete billing information to give to their own clients.
The ENAiKOON construction equipment monitoring solution
The flexible telematics solution that ENAiKOON offers can be tailored to
each customer as exemplified in the above case. Start saving time, increase
productivity, and improve rental equipment management with the construction equipment
monitoring system. Contact ENAiKOON
today for your free trial. Locate series to the rescue in the Netherlands
 Another stolen van was returned to its grateful owner in the Netherlands thanks
to the locate series device that was installed in it. The thieves were unaware
that Generali Verzekeringsgroep had the foresight to install tracking devices
in their vans and cars and that when the van was then stolen, that their every
movement was being tracked in real-time in ENAiKOON’s web portal.
Another stolen van was returned to its grateful owner in the Netherlands thanks
to the locate series device that was installed in it. The thieves were unaware
that Generali Verzekeringsgroep had the foresight to install tracking devices
in their vans and cars and that when the van was then stolen, that their every
movement was being tracked in real-time in ENAiKOON’s web portal.
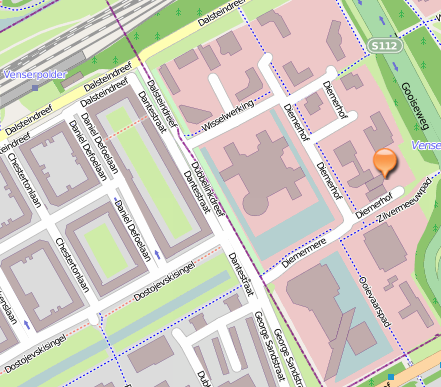 When an employee of Generali, who had parked the van in front of his house,
noticed that it was no longer there he immediately called his supervisor. With
a quick look in the ENAiKOON web portal they were able to determine exactly
where the van was. The thieves had driven it across town and it was parked on a
quiet residential street. At this point Generali decided to inform the
authorities about what had happened. The police then wanted to watch the van to
try and catch the perpetrators.
This was an excellent plan on the part of the local police, because of this
one criminal was apprehended. At first the van was towed to the police head
quarters for a search. There they discovered tools that were most likely used
for already or would in the future be used for a burglary. The thieves had
tried to manipulate the motor management system of the vehicle as well. A
mechanic then had a look over the van, but is now back in the hands of its
rightful owners. Thanks to the ENAiKOON device and the quick thinking on behalf
of the local police there is also one less criminal on the streets in the
Netherlands.
When an employee of Generali, who had parked the van in front of his house,
noticed that it was no longer there he immediately called his supervisor. With
a quick look in the ENAiKOON web portal they were able to determine exactly
where the van was. The thieves had driven it across town and it was parked on a
quiet residential street. At this point Generali decided to inform the
authorities about what had happened. The police then wanted to watch the van to
try and catch the perpetrators.
This was an excellent plan on the part of the local police, because of this
one criminal was apprehended. At first the van was towed to the police head
quarters for a search. There they discovered tools that were most likely used
for already or would in the future be used for a burglary. The thieves had
tried to manipulate the motor management system of the vehicle as well. A
mechanic then had a look over the van, but is now back in the hands of its
rightful owners. Thanks to the ENAiKOON device and the quick thinking on behalf
of the local police there is also one less criminal on the streets in the
Netherlands.
 According to Hans Verhaar the Expertisedienst Manager at Generali
Verzekeringsgroep “When our van was stolen we were at first shocked. Then we
looked in inViu pro to see the location of the vehicle. We were able to find
our van and then we told the police exactly what had happened. It was recovered
and one person was arrested as a result. Thanks to the device from ENAiKOON we
were able to recover our vehicle easily without a lot of hassle. We knew
immediately where to go to retrieve it and could tell the police where it was
located.”
According to Hans Verhaar the Expertisedienst Manager at Generali
Verzekeringsgroep “When our van was stolen we were at first shocked. Then we
looked in inViu pro to see the location of the vehicle. We were able to find
our van and then we told the police exactly what had happened. It was recovered
and one person was arrested as a result. Thanks to the device from ENAiKOON we
were able to recover our vehicle easily without a lot of hassle. We knew
immediately where to go to retrieve it and could tell the police where it was
located.” 



